Monitoring traffic patterns and logs for suspicious activity involves continuously observing network data flows and system logs to detect anomalies, unauthorized access, or malicious behaviour that could indicate security threats such as intrusions, malware, or insider attacks.
Key components and methods include:
-
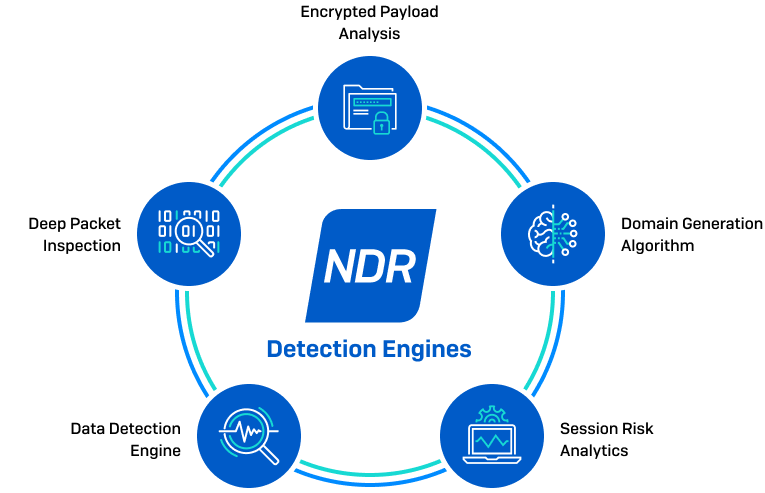
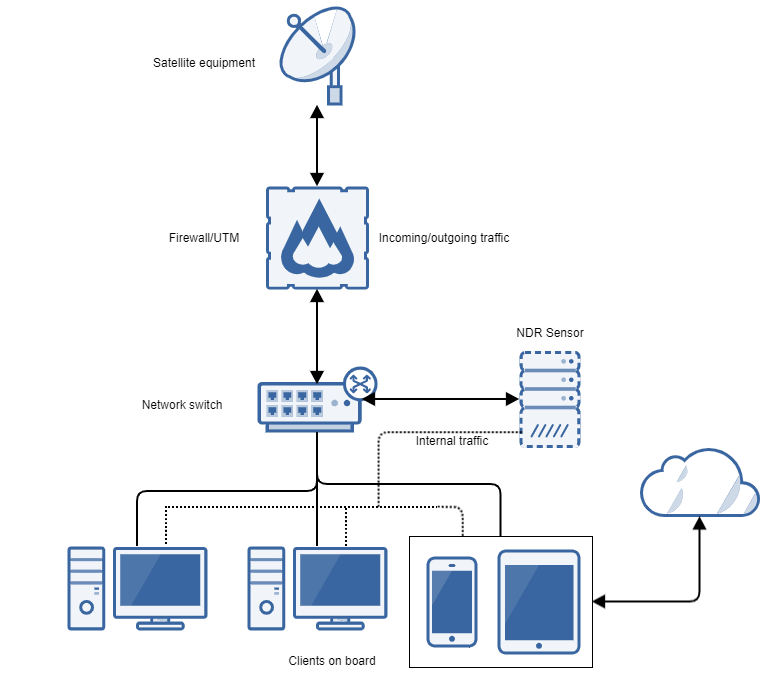
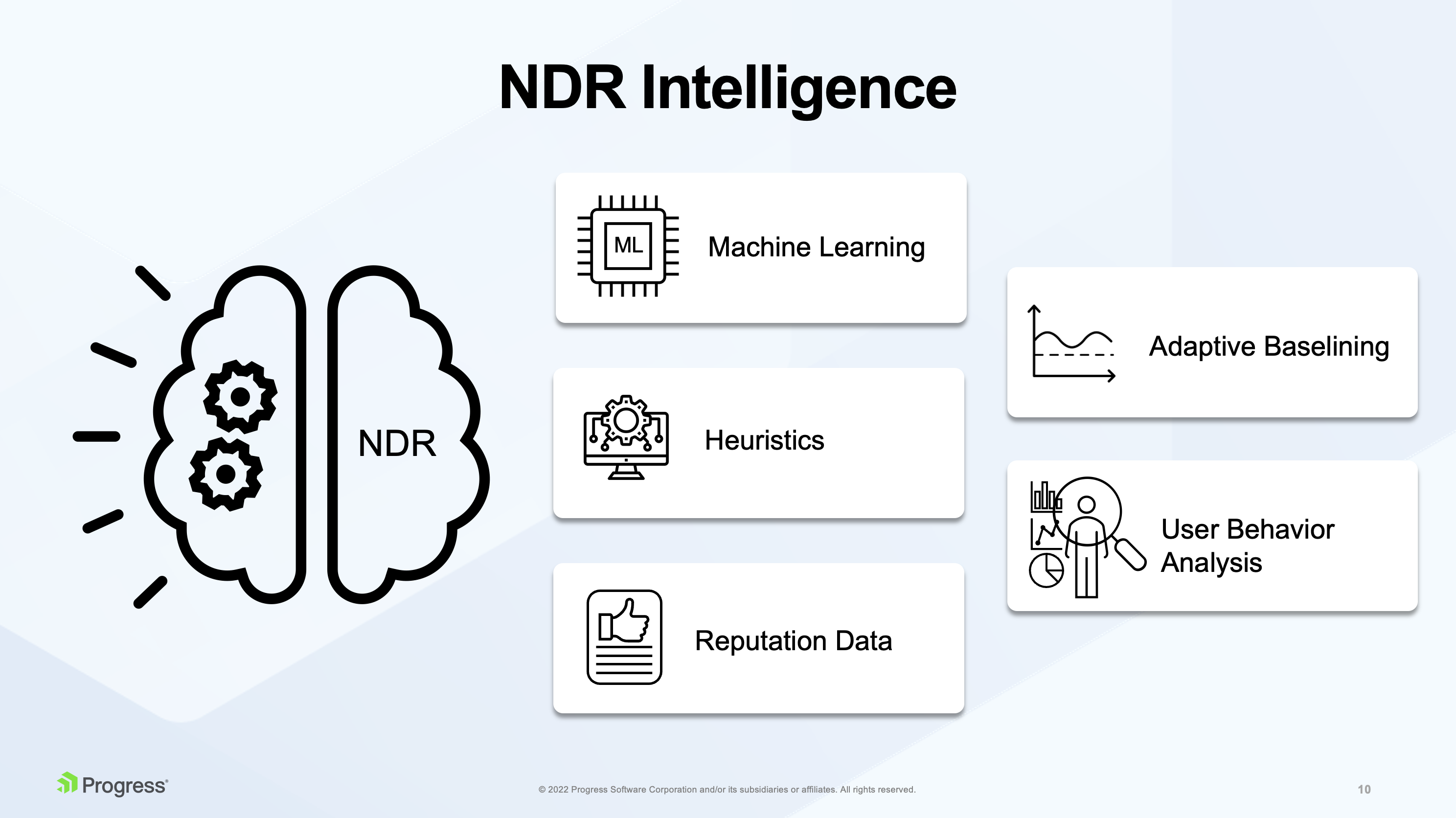
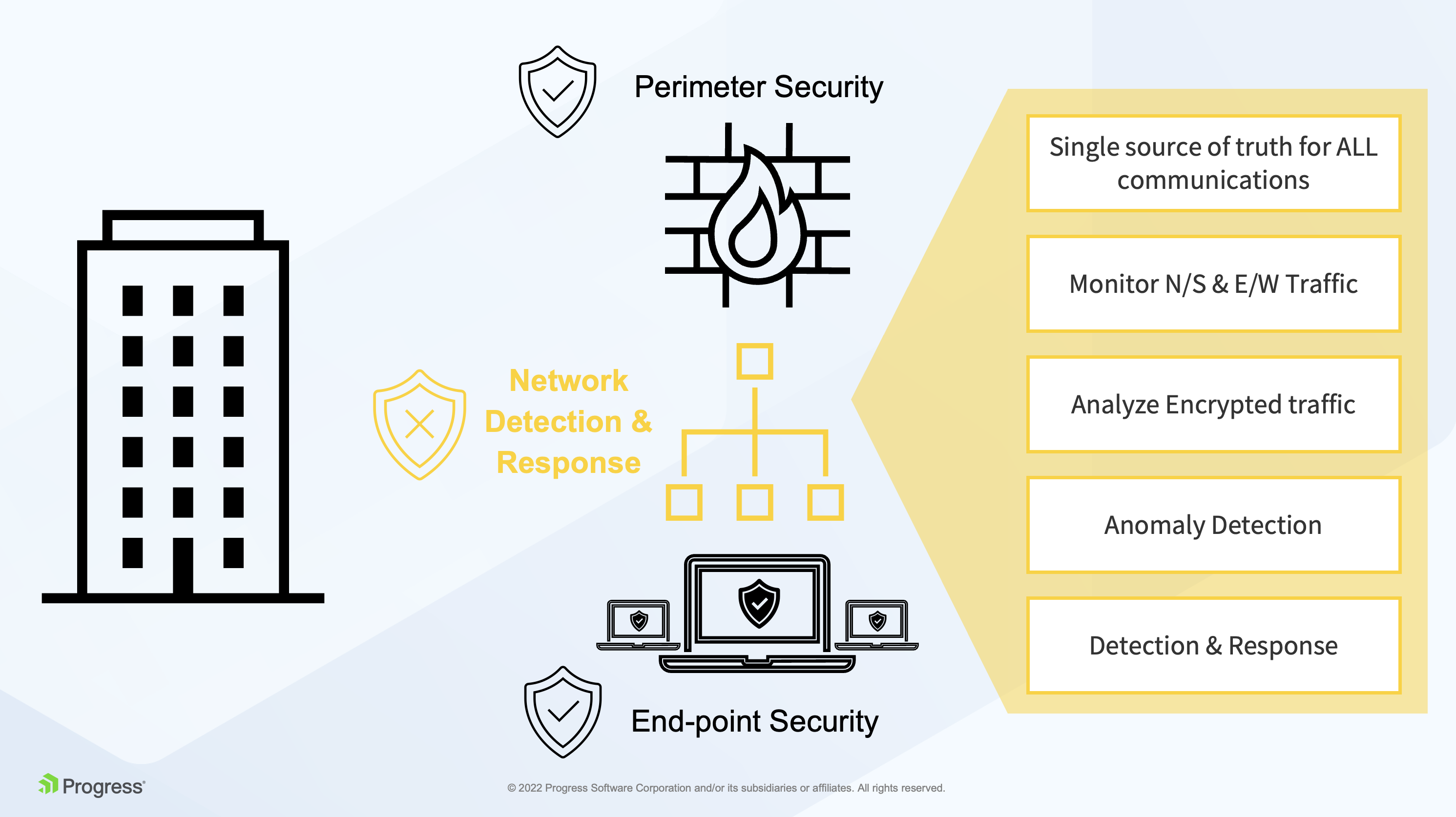
Network Detection and Response (NDR): Tools like Sophos NDR monitor deep network traffic beyond firewalls and endpoints to detect abnormal flows from unmanaged devices, rogue assets, insider threats, zero-day attacks, and command-and-control communications. They integrate with endpoint and firewall systems to provide automated threat detection and response in real time.
-
Intrusion Detection Systems (IDS): IDS passively monitor network traffic or host logs to identify suspicious activity. They use:
- Signature-based detection to match known attack patterns.
- Anomaly-based detection to flag deviations from established normal behaviour baselines, enabling detection of unknown or zero-day threats. IDS generate alerts for suspicious events like brute-force attempts or unauthorized port access and can integrate with other security tools for response actions.
-
Network Traffic Analysis (NTA): NTA tools analyze traffic at network edges and cores to identify operational and security anomalies such as ransomware activity, data exfiltration, unusual bandwidth usage, and unauthorized access. They provide visibility into device inventories, user activity, and generate reports for forensic and management purposes.
-
Logging and Monitoring Best Practices:
- Develop a monitoring plan identifying critical assets, risks, and log retention policies.
- Centralize logs using Security Information and Event Management (SIEM) tools for efficient analysis.
- Protect log integrity with cryptographic measures.
- Establish baseline network behaviour to detect anomalies.
- Monitor outbound connections and unauthorized data transfers to detect compromised hosts or data breaches.
- Deploy monitoring agents at network boundaries to detect unknown external connections.
-
Detection of Specific Threats: Monitoring can identify patterns indicative of Distributed Denial-of-Service (DDoS) attacks, phishing attempts, malware command-and-control traffic, and insider threats by analyzing traffic volumes, access patterns, and unusual login times.
In summary, effective monitoring combines multiple technologies—NDR, IDS, NTA, and centralized logging—to provide comprehensive visibility into network traffic and logs, enabling early detection and automated or manual response to suspicious activities and cyber threats.
















Maple Ranking offers the highest quality website traffic services in Canada. We provide a variety of traffic services for our clients, including website traffic, desktop traffic, mobile traffic, Google traffic, search traffic, eCommerce traffic, YouTube traffic, and TikTok traffic. Our website boasts a 100% customer satisfaction rate, so you can confidently purchase large amounts of SEO traffic online. For just 720 PHP per month, you can immediately increase website traffic, improve SEO performance, and boost sales!
Having trouble choosing a traffic package? Contact us, and our staff will assist you.
Free consultation